Cyber Essentials is a UK government-backed certification scheme designed to help organisations protect themselves against common cyber attacks. For many London businesses, particularly those working with the public sector or larger enterprises, it's becoming a prerequisite for doing business. It's a foundational element of any information security programme.
What is Cyber Essentials?
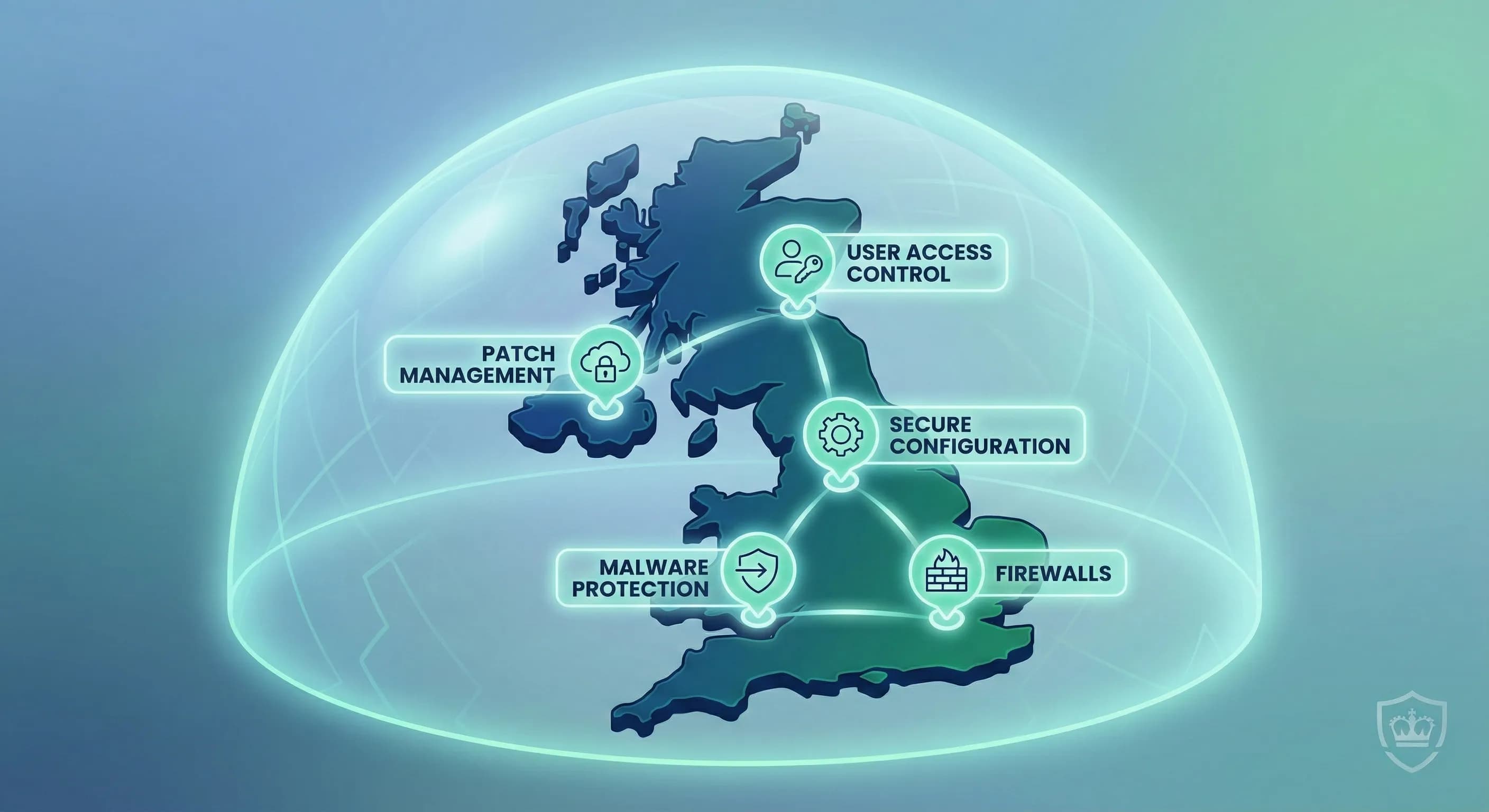
Cyber Essentials focuses on five key controls that, when properly implemented, can prevent around 80% of cyber attacks:
- Firewalls: Controlling what traffic can enter and leave your network
- Secure Configuration: Ensuring devices are configured securely
- User Access Control: Managing who has access to what
- Malware Protection: Defending against viruses and other malicious software
- Patch Management: Keeping software up to date
These controls form the foundation of our cybersecurity services approach.
Two Levels of Certification
Cyber Essentials
The basic level involves a self-assessment questionnaire verified by an external certification body. It's suitable for organisations wanting to demonstrate basic security hygiene.
Cyber Essentials Plus
This adds an external technical verification where an assessor tests your systems. It provides stronger assurance and is often required for handling sensitive data or government contracts.
Why Get Certified?
Business Requirements
- Mandatory for UK government contracts involving personal data
- Increasingly required by enterprise clients and supply chains
- Demonstrates commitment to security to clients and partners
Security Benefits
- Provides a framework for basic security controls
- Identifies gaps in your current security posture
- Creates a foundation for more advanced certifications
Insurance and Liability
- May reduce cyber insurance premiums
- Demonstrates due diligence in the event of an incident
- Free cyber liability insurance included with certification
The Certification Process
Step 1: Scope Definition
Define what's in scope for certification. This typically includes all devices and systems that handle business data. Be realistic about your scope—artificially limiting it may reduce the value of certification.
Step 2: Gap Assessment
Review your current state against the five controls:
- Do you have boundary firewalls and internet gateways?
- Are all devices configured securely with default passwords changed?
- Do you control user accounts and access privileges?
- Is malware protection installed and active on all devices?
- Are all software and devices patched within 14 days of updates?
Step 3: Remediation
Address any gaps identified. Common issues include:
- Out-of-date software on some devices
- Inconsistent security configurations
- Users with unnecessary admin privileges
- Missing or outdated malware protection
Step 4: Self-Assessment
Complete the assessment questionnaire through an accredited certification body. Answer honestly—the questions are designed to verify your controls are genuinely in place.
Step 5: Technical Verification (Plus only)
For Cyber Essentials Plus, an assessor will:
- Scan your external IP addresses for vulnerabilities
- Test internal workstations for security controls
- Verify malware protection is active
- Check patch levels across sampled devices
Common Challenges
BYOD and Personal Devices
If employees use personal devices for work, you need to decide whether to include them in scope or implement policies to exclude work data from personal devices.
Cloud Services
SaaS applications are generally outside scope if properly configured, but you remain responsible for user access control and secure configuration of your accounts.
Remote Workers
Home networks and personal routers create complexity. Consider VPN requirements and endpoint protection for remote devices.
Timeline and Costs
For a typical SMB:
- Cyber Essentials: Can be achieved in 2-4 weeks if controls are already in place; certification costs from £300-500
- Cyber Essentials Plus: Usually 4-8 weeks including assessor scheduling; costs from £1,500-3,000 depending on scope
Getting Support
While smaller organisations can achieve Cyber Essentials independently, working with an experienced managed IT partner can:
- Quickly identify and remediate gaps
- Ensure controls are implemented correctly first time
- Provide evidence and documentation for the assessment
- Help prepare for the technical verification (Plus)
- Maintain compliance between annual recertifications
For London businesses looking to achieve Cyber Essentials certification efficiently, we offer a structured programme that combines gap assessment, remediation support, and certification preparation into a streamlined package. Our IT consulting services can help you build a security roadmap that goes beyond basic compliance.